We use cookies to improve our services. By continuing to navigate the site, you agree to the terms of use of cookies.
Map of GlobalNet backbone networks
Filters
Map search
14 Jun 2023
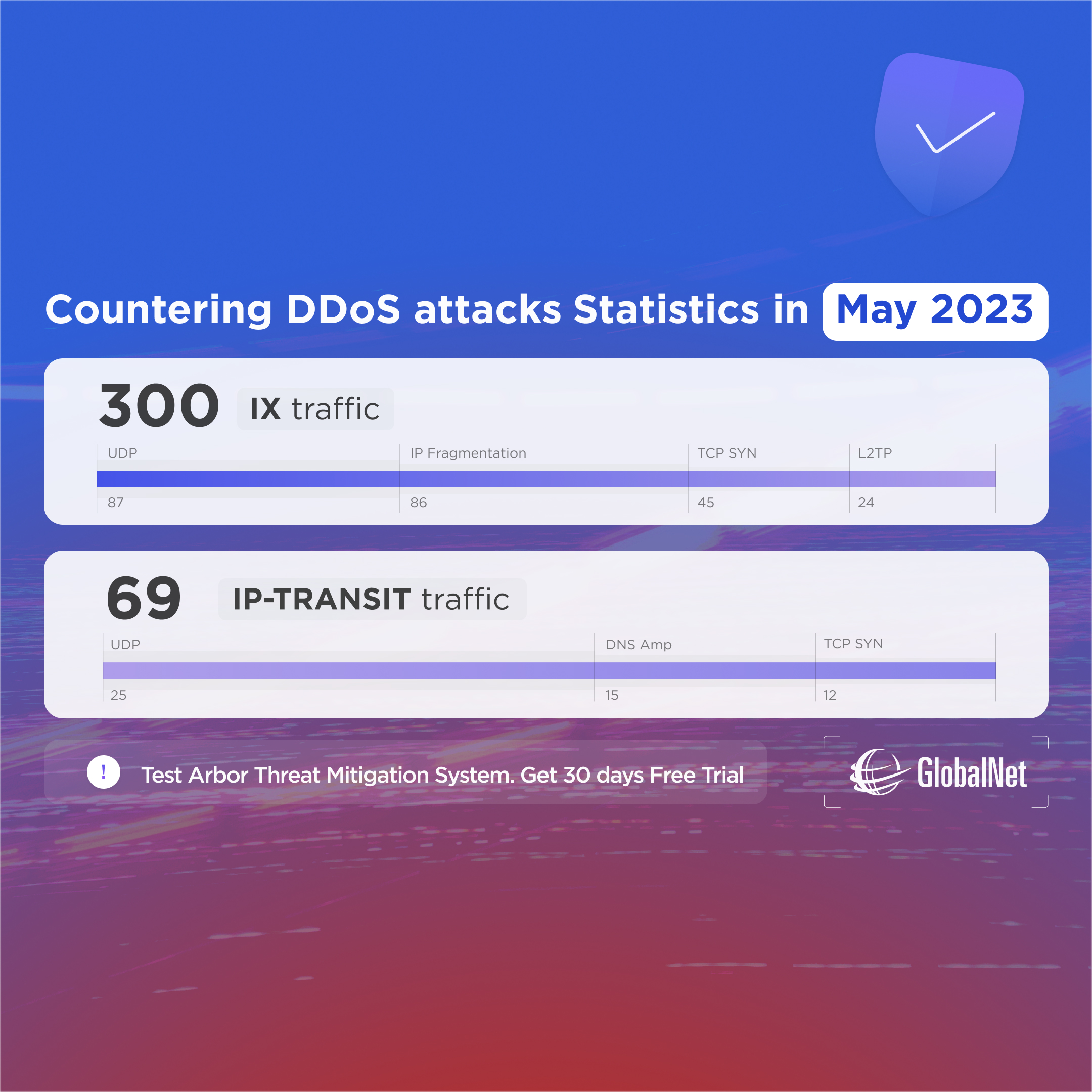
DDoS attack protection statistics in May
As always we are publishing the statistics of threats detection and protection in the last month. This time we are going to discuss in detail an example of a massive attack on our client’s network that was effectively protected by our DDoS Protection service.
Last month there was a major hosting provider client that was under a destructive DDoS attack within IP-Transit service. This attack in the core was particularly dangerous due to a large amount of harmful signatures, such as TCP SYN, UDP, DNS Amplification. The Arbor Sightline detection and protection system automatically generated defensive flowspec rules, blocking the malicious attack as UDP traffic within GlobalNet network.
Nonetheless, the client’s SOC system kept registering the harmful TCP traffic reaching the server and overloading the system. By combining the data from the Arbor Sightline and server request logs of the client we managed to detect the source of the threat. It was blocked using the additional flowspec rules restricting access to the server based on the detected and analyzed attack patterns.